Chapter summary
Each individual’s personal risk profile is shaped by vulnerabilities and strengths, influenced by how they are perceived by others. An inclusive approach to security risk management challenges stereotypes that label certain profiles as inherently more vulnerable, while considering specific risk factors that may be overlooked in a homogenous approach.
Identity-based risks can relate to factors such as race, ethnicity, nationality, disability, culture, religion, gender, sexuality and socio-economic status, as well as combinations of these factors. Sources of threat can be both internal and external to the organisation. In hostile work cultures, minor incidents can escalate into more severe forms of aggression.
Some identity characteristics, like sexual orientation or hidden disabilities, are invisible, highlighting the need for an inclusive security risk management approach that assumes diverse needs, encourages dialogue and empowers staff to raise concerns. Additionally, while location-based risks are important, whether a location is ‘safe’ often depends more on the individual’s identity and how they are perceived than on the location itself, requiring a shift in focus from ‘where is safe’ to ‘who is safe’.
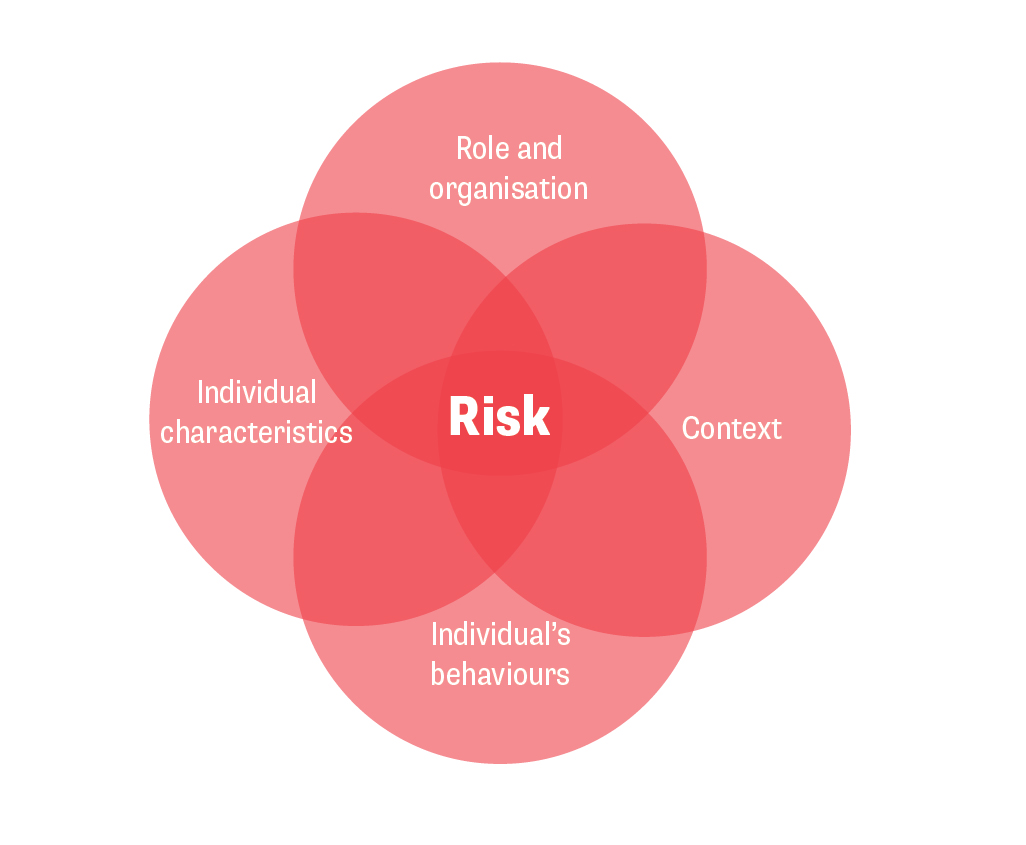
In practice, a person-centred approach involves recognising profile-specific risks due to the intersection of individual characteristics (intersectional identity) and behaviour, organisational factors and the context in which staff are working (both in the physical and digital spheres) (see figure below), and tailoring security measures to specific needs and vulnerabilities. While a focus on individual differences can raise fears about potential discrimination, this can be avoided through collaborative policy development, clear communication, and feedback mechanisms that ensure security practices are consultative, equitable, fair and adaptable.